
Virtualization for Your Business
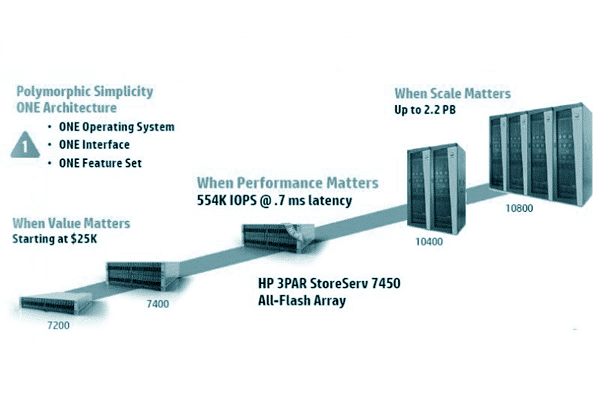
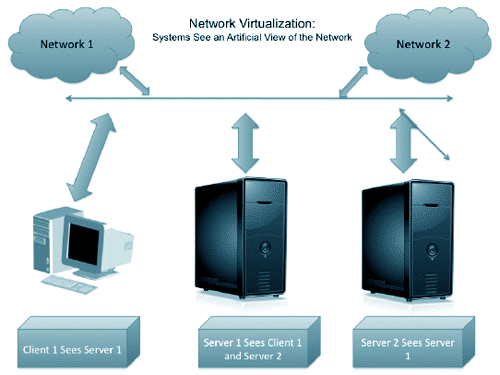
If your business success relies much on networked IT resources, it’s good to consider virtualization. With virtualization you can abstract applications and as well as their related components away from the supporting hardware, and you can get a virtual (logical)...
Big Players Eye the Big Data Minefield
These days there’s much talk in IT circles about big data. No, it’s not a new phenomenon taking the world by storm. Neither is it about data having morphed into something so huge that the earth may no longer be enough to contain it. Rather, it’s more of super...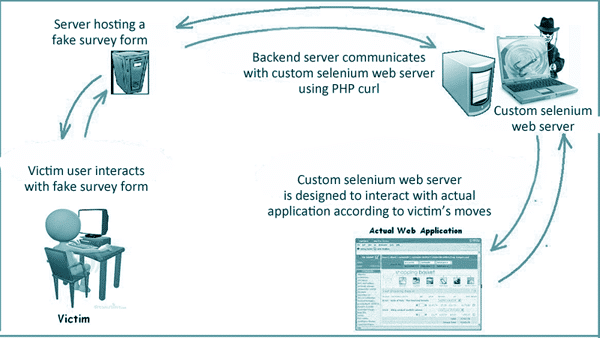
Ever Heard of Whaling?
Yes, you read it right. Whaling. And it’s different from whale fishing, the controversial business of catching whales for profit taking place in certain parts of the world. And speaking of fishing, this brings to mind the homophonic term phishing that has become...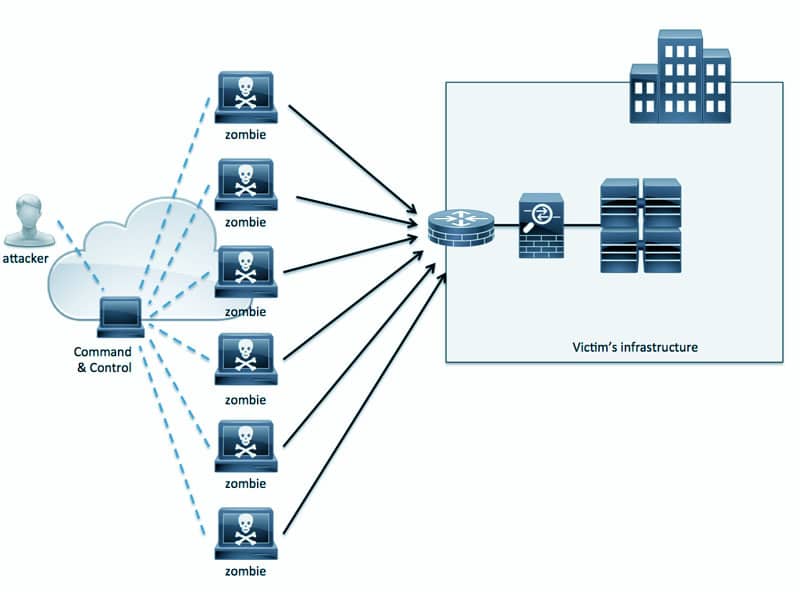
DDoS Attacks Hurt the Pocket
Distributed denial of service (DDoS) is a type security threat wherein one individual or group — the attacker — intentionally and maliciously lets loose extremely high volumes of Internet traffic into the computer network resources of another — the victim — in order...

 Server deployment
Server deployment Server support
Server support Extended server support
Extended server support Managed servers
Managed servers