IT Efficiency Through Converged Infrastructure
The idea of converged infrastructure revolves around forming a single optimized IT package by putting together several components to meet present-day business needs. According to HP, converged infrastructure meets these needs “by bringing storage, servers, networking,...Systems Can Be Attacked Via NTP Flaws
At least three serious vulnerabilities in the Network Time Protocol (NTP) have been uncovered by security researchers at Google in 2014. This is quite serious because of the sheer number of computers that may potentially be targets of DDoS (click here to read earlier...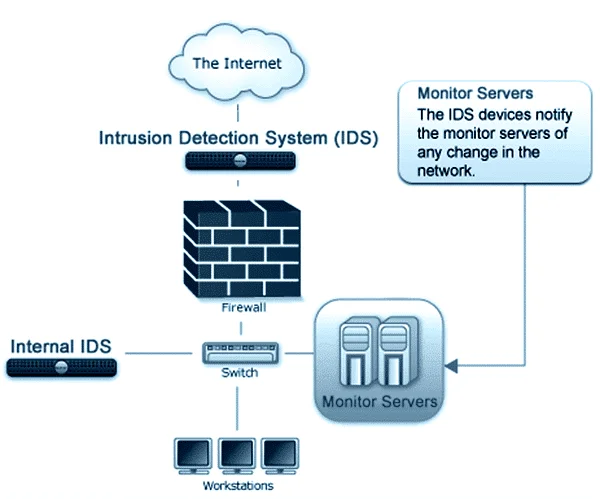
Who Needs an Intrusion Detection System?
Intrusion detection systems (also called ID systems and IDS) have been, and are still constantly being developed in response to past and present attacks on many high-profile websites and networks, including those of Sony, eBay, Yahoo Mail, Google, Apple iCloud, UPS,...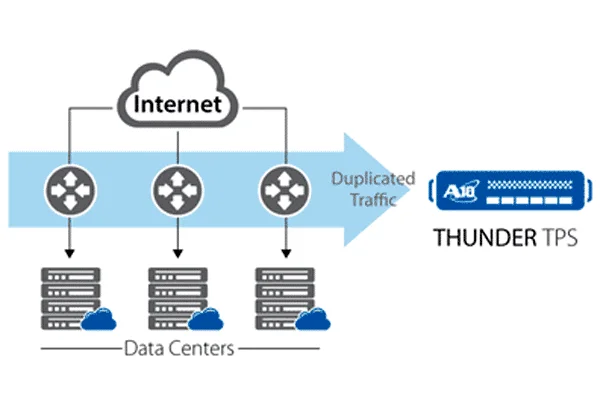

 Server deployment
Server deployment Server support
Server support Extended server support
Extended server support Managed servers
Managed servers